By: Rolla Hassan Ph.D
Introduction
The proliferation of 5G networks is on a rapid trajectory, with projections indicating approximately 2.4 billion connections by 2025. This expansion is accompanied by a proportional increase in the cyber-attack surface and threat sophistication. Distributed Denial of Service (DDoS) attacks, for instance, have seen volume increases of 200 to 300 percent. The 5G core, a software-defined, distributed system responsible for processing immense data volumes and connecting billions of endpoints, represents a high-value target for malicious actors.
A Zero Trust Architecture (ZTA) offers a robust security model tailored for this dynamic environment. Its fundamental tenets—never trust, always verify; assume breach; and enforce least-privilege access—mandate that every access request be rigorously authenticated and authorized, irrespective of its origin. When applied to the 5G core, ZTA provides a granular, identity-centric security framework that protects network functions, users, devices, APIs, and network slices. This model is uniquely suited to the software-based, distributed nature of 5G, enabling secure, high-speed traffic flow while mitigating lateral threat movement and safeguarding critical network functions.
This analysis provides a technical examination of the core principles, benefits, and implementation challenges of applying a Zero Trust model to 5G core networks, offering insights into creating a resilient and secure next-generation telecommunications infrastructure.
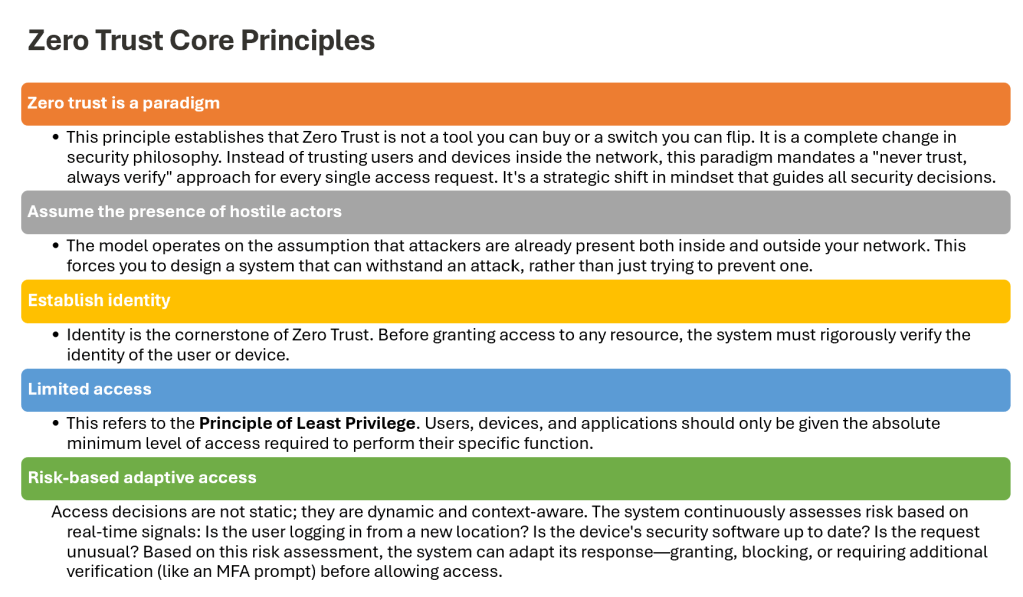
Core Principles of Zero Trust in 5G Networks
In the context of the 5G core, a Zero Trust model mandates that every transaction is independently verified, all network paths are explicitly controlled, and access is granted on a strict least-privilege basis. These principles are applied to secure control plane functions, API endpoints, and network slices without introducing prohibitive latency. The primary objectives are to minimize the blast radius of a potential breach, prevent lateral movement of threats, and enable early threat detection.
Continuous Authentication and Authorization
Static, one-time authentication is insufficient for the dynamic nature of 5G services. A ZTA demands continuous validation of identity and context for all entities, including users, devices, network functions, and APIs. Authentication and authorization must occur at the initiation of a session and be dynamically re-evaluated in response to changes in risk posture, such as shifts in device health, location, or behavioral anomalies.
Key Technical Practices:
- Multi-Factor and Context-Aware Authentication: Combine strong identity signals, such as SIM/eSIM credentials, with robust user authentication methods and device trust indicators. Access tokens should be frequently rotated and cryptographically bound to the session’s context (e.g., device ID, location, network slice).
- Dynamic, Policy-Driven Authorization: Employ advanced policy engines that re-evaluate access permissions for every API call or service request. If a device’s security posture degrades or its behavior deviates from established baselines, the policy engine can automatically revoke or downgrade access in real time.
- Scoped, Short-Lived Credentials: Issue ephemeral, narrowly scoped access tokens for interactions with core network functions like the Network Exposure Function (NEF) and Network Repository Function (NRF). This practice eliminates the risks associated with static, broadly permissive API keys.
Scenario: A network engineer initiates a remote management session from a corporate laptop to perform maintenance on core functions. The session is established following multi-factor authentication (MFA) and a device compliance check. If the engineer’s device subsequently connects to an untrusted Wi-Fi network, the continuous authorization system detects this change in context and automatically downgrades the session privileges from administrative control to read-only access until the device returns to a trusted state.
Micro-Segmentation
Micro-segmentation involves logically partitioning the 5G core into granular, isolated zones, with access control policies enforced at the boundary of each zone. This approach ensures that network locality does not confer implicit trust; communication between segments is denied by default and only permitted based on explicit, policy-defined rules.
Implementation in a 5G Core:
- Per-Function and Per-Service Zones: Isolate critical network functions—such as the Access and Mobility Management Function (AMF), Session Management Function (SMF), Unified Data Management (UDM), and User Plane Function (UPF)—into distinct security segments with strict, pre-defined communication allow-lists.
- API-Level Policy Enforcement: Implement fine-grained policies that govern service-to-service communication between Network Functions (NFs). Every API call must be authenticated, authorized, and logged, ensuring that only legitimate interactions occur.
- Network Slice Isolation: Treat each network slice as an independent, self-contained security domain. A breach within a consumer mobile broadband (eMBB) slice is thereby prevented from propagating to a high-security enterprise or ultra-reliable low-latency communications (URLLC) slice.
Scenario: An attacker successfully compromises a low-cost IoT device operating within a massive Machine-Type Communications (mMTC) slice. Due to micro-segmentation, the attacker’s attempts to move laterally to access the control plane or other network slices are blocked at the segment boundary. The breach is effectively contained, simplifying remediation and minimizing service impact.
Real-Time Monitoring and Analytics
The high-volume, high-velocity nature of 5G traffic necessitates advanced, real-time visibility and threat detection capabilities. AI and machine learning-driven analytics are essential for identifying subtle anomalies and behavioral deviations that traditional, rule-based systems would miss.
Key Monitoring Capabilities:
- User and Entity Behavior Analytics (UEBA): Establish dynamic baselines of normal behavior for subscribers, administrators, and network functions. UEBA can flag deviations such as anomalous API call frequencies, unusual roaming patterns, or policy modifications occurring outside of standard operational windows.
- Control Plane and API Telemetry Analysis: Continuously monitor traffic between network functions (e.g., Nnrf, Naf interfaces) and service mesh communications for anomalies, authentication failures, and policy violations.
- Automated Response Actions: Integrate the analytics platform with policy engines to enable automated, rapid responses. These can include quarantining a compromised network slice, throttling a misbehaving service, or forcing re-authentication for a user or device exhibiting high-risk behavior.
Scenario: A UEBA system detects a statistically significant increase in failed authentication token exchanges between an SMF and a UDM. This pattern suggests a potential credential misuse or brute-force attack. The system automatically elevates the risk score associated with the involved entities, triggering the policy engine to tighten access scopes and initiate credential rotation, thereby neutralizing the threat path without disrupting legitimate user sessions.
Strategic Benefits of a 5G Zero Trust Architecture
Adopting a Zero Trust model provides tangible security and operational benefits for telecom operators, enhancing resilience without compromising the performance demands of 5G. It reduces the potential impact of a breach, improves access governance, and enables intelligent, automated threat detection and response.
Enhanced Resilience Against Cyber Attacks
By discarding the concept of a trusted internal network, ZTA fundamentally strengthens a network’s defense posture. Every user, device, and API call must be authenticated and authorized, significantly reducing the attack surface. In the event of a breach, micro-segmentation acts as a critical containment mechanism, preventing threat actors from moving laterally from a compromised workload to sensitive functions like the AMF, SMF, or UDM.
Practical Implications:
- Default Containment: A compromised IoT endpoint or user device is isolated, preventing the breach from escalating into a core network compromise.
- Reduced Value of Stolen Credentials: The reliance on short-lived, dynamically generated tokens means that even if credentials are stolen, their window of usability is extremely limited.
- Verifiable Internal Security: All internal service-to-service communication is subject to authentication and logging, eliminating blind spots and providing a comprehensive audit trail.
Granular Control and Access Governance
ZTA enables operators to enforce dynamic, context-aware access policies that combine role-based permissions with real-time device posture and environmental checks. This ensures that only authorized entities can access specific network functions under appropriate conditions.
Operational Gains for Operators:
- Contextual Access Enforcement: An engineer’s access rights can be dynamically adjusted based on their role, device compliance status, and physical location, enforcing the principle of least privilege.
- Accelerated Secure Operations: Policy engines can validate and approve legitimate, low-risk requests in milliseconds, ensuring that security checks do not impede operational velocity.
- Secure Multi-Tenancy with Slicing: Each network slice (e.g., enterprise, consumer, URLLC) can be managed with its own distinct set of access policies, minimizing the risk of cross-slice data leakage or interference.
Intelligent Threat Detection and Response
AI-powered analytics provide the necessary intelligence to detect sophisticated threats in real time. By learning the normal operational patterns of the 5G network, these systems can identify subtle anomalies that indicate credential misuse, API abuse, or unauthorized data exfiltration.
Key Outcomes:
- Proactive Threat Identification: A sudden spike in failed API calls between an SMF and UDM can be flagged as a high-risk event before it escalates.
- Targeted and Automated Remediation: The system can trigger precise, automated responses, such as forcing re-authentication for a specific user, rotating API keys for a service, or isolating an entire network slice.
- Improved Service Availability: By enabling rapid, targeted containment of threats, ZTA helps prevent widespread service outages, ensuring a better customer experience and reducing revenue loss.
Implementation Strategy: Challenges and Solutions
While the benefits are compelling, implementing a Zero Trust Architecture in a 5G core network is a complex undertaking. Operators must navigate challenges related to legacy system integration, performance overhead, and operational complexity. A phased, strategic approach is crucial for a successful rollout.
Common Implementation Hurdles
- Hybrid and Legacy System Complexity: Most operators manage a heterogeneous environment comprising 4G Evolved Packet Core (EPC) elements, 5G Standalone (SA) components, private network deployments, and multi-cloud infrastructure. Creating and enforcing consistent security policies across these disparate domains is a significant challenge.
- Performance and Latency Concerns: The “always verify” principle introduces additional processing for authentication, authorization, and logging. If not implemented efficiently, these checks could increase control plane latency or reduce User Plane Function (UPF) throughput, potentially violating 5G’s strict performance requirements.
- Operational and Financial Overhead: Deploying and managing new security infrastructure—including identity providers, public key infrastructure (PKI), service meshes, and policy engines—incurs both capital and operational costs. Furthermore, teams may require new skills to develop and maintain the granular policies required for a ZTA.
A Phased and Strategic Rollout
A pragmatic implementation strategy focuses on incremental adoption, prioritizing high-risk areas while leveraging cloud-native technologies to manage complexity and cost.
- Discovery and Asset Mapping: Begin with a comprehensive inventory of all network functions, APIs, data flows, and identity stores across the RAN, edge, and core. This initial mapping should identify high-value assets, such as the UDM, AUSF, and billing systems, which should be prioritized for protection.
- Adopt a Hybrid Approach: Avoid a “big bang” migration. Initially, apply Zero Trust controls to the most critical new services, such as the 5G Service-Based Architecture (SBA) APIs, by enforcing mutual TLS (mTLS) and OAuth 2.0 with short-lived tokens. Legacy 4G/EPC flows can remain under existing security models pending a future migration.
- Leverage Cloud-Native Security Primitives: Utilize a service mesh to automate mTLS, enforce traffic policies, and provide observability for communication between network functions. Centralize identity management using modern protocols like OpenID Connect (OIDC) and OAuth 2.0, and automate certificate management to reduce operational burden.
- Integrate AI for Intelligent Monitoring: Deploy UEBA to analyze control plane and API telemetry. Use machine learning models to detect anomalies and trigger automated, proportionate responses, such as forcing re-authentication or rate-limiting suspicious traffic, thereby reducing the mean time to detect (MTTD) and respond (MTTR).
- Enforce Granular Micro-segmentation: Implement strict isolation between network slices, treating each as a distinct security perimeter with its own policies, cryptographic keys, and logs. Within the core, enforce deny-by-default policies for the control plane, allowing communication only through explicitly defined and secured API pathways.
Conclusion
The Zero Trust model is not merely a security enhancement but a fundamental architectural shift that aligns with the cloud-native, API-driven design of 5G core networks. By enforcing continuous verification, granular segmentation, and intelligent, real-time monitoring, operators can significantly reduce their attack surface, contain threats effectively, and maintain the high-performance standards required by 5G. The transition requires careful planning and a phased approach, but the resulting gains in security, resilience, and operational control are essential for the long-term success and trustworthiness of next-generation telecommunications. The time to begin this strategic initiative is now, starting with a thorough assessment and a pilot project focused on a high-value network slice or service.
References
Ericsson. (2021). “Zero trust and 5G.” Ericsson Technology Review. [Online]. Available: https://www.ericsson.com/en/reports-and-papers/ericsson-technology-review/articles/zero-trust-and-5g.
Cybersecurity and Infrastructure Security Agency (CISA ). (2024). “Zero Trust Microsegmentation Guidance Part One: Strategy.” [Online]. Available: https://www.cisa.gov/sites/default/files/2025-07/ZT-Microsegmentation-Guidance-Part-One_508c.pdf.
Nokia Bell Labs. (n.d. ). “Realizing zero trust architecture for 5G networks.” Nokia Bell Labs Consulting. [Online]. Available: https://www.nokia.com/bell-labs/bell-labs-consulting/articles/realizing-zero-trust-architecture-for-5g-networks/.
S. H. R. Kazmi, M. R. Asghar, and R. Dautov. (2022 ). “A holistic review of the worth of zero-trust security solutions.” Computers & Security, vol. 123, art. 102932. [Online]. Available: https://www.sciencedirect.com/science/article/abs/pii/S0167404822003042.
CSG. (n.d. ). “Why is Zero Trust Security Essential in a Data-Rich 5G World?” CSG Insights. [Online]. Available: https://www.csgi.com/insights/why-is-zero-trust-security-essential-in-a-data-rich-5g-world/.
M. A. Beg, M. R. Asghar, and M. S. Khan. (2024 ). “Zero Trust in 5G Networks: Principles, Challenges, and Opportunities.” TechRxiv. [Online]. Available: https://www.techrxiv.org/users/793184/articles/1229171-zero-trust-in-5g-networks-principles-challenges-and-opportunities.
Tufin. (2023 ). “3 Challenges (and Solutions) to Implementing Zero Trust.” Tufin Blog. [Online]. Available: https://www.tufin.com/blog/3-challenges-and-solutions-implementing-zero-trust.
OneLayer. (n.d. ). “Implementing NIST Zero Trust in Private 5G/LTE.” [Online]. Available: https://onelayer.com/implementing-nist-zero-trust-in-private-5g-lte/.



Leave a reply to 5G Network API Security: 2026 Technical Guide – Pixelsseo Cancel reply